If you’ve ever wanted to monitor and filter through network traffic in realtime, ngrep is about to be your new best friend.
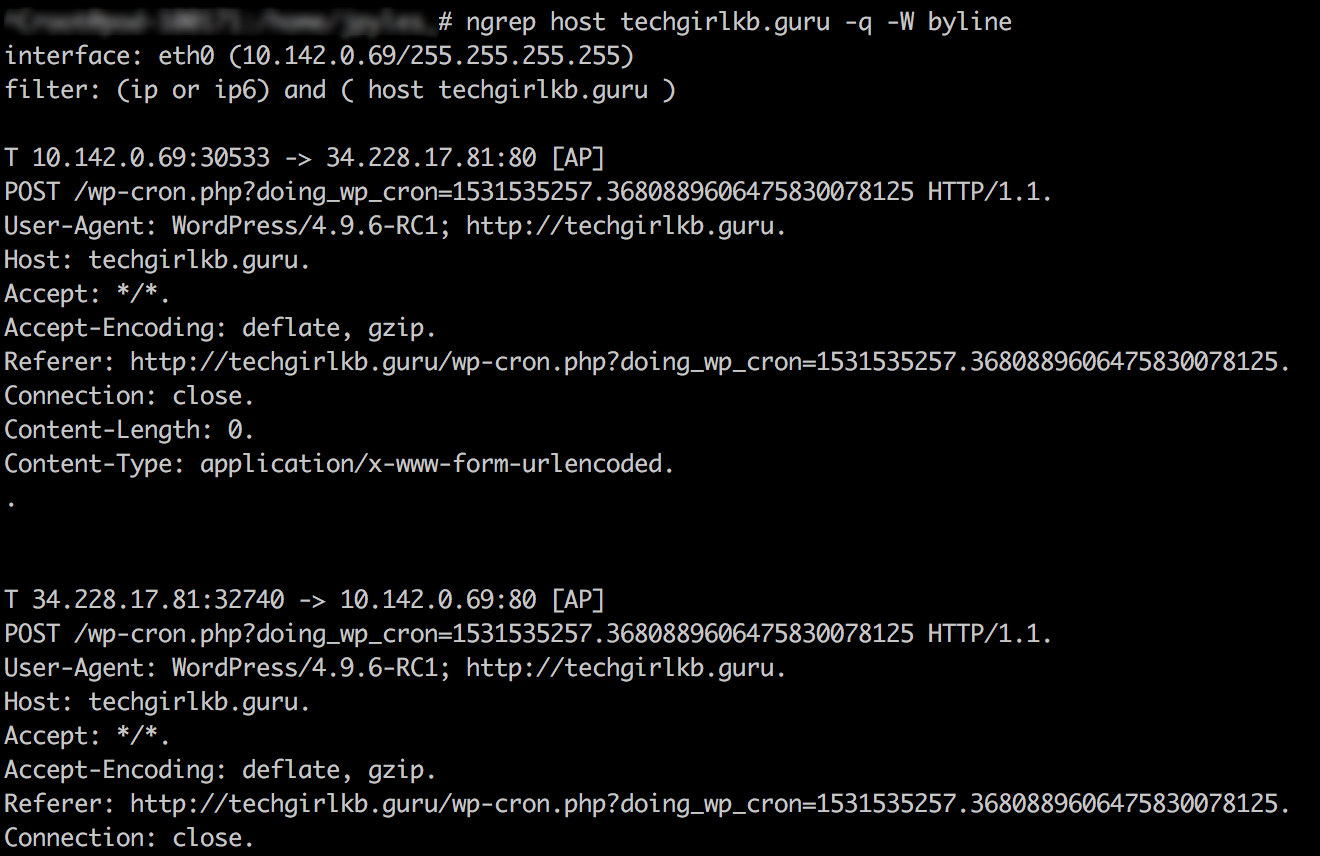
ngrep stands for “network grep” and can be a very useful tool for packet sniffing, troubleshooting, and more. It’s like standard GNU grep (which I talk about a lot in my parsing logs article) but for the network layer. That means you can use regex (or regular expressions) to filter and parse through active network connections. Check out some common examples in the ngrep documentation here. In the following sections we’ll explore what packet sniffing is and why it might be useful to you.
What is packet sniffing?
In short, packet sniffing allows you to inspect the data within each network packet transmitted through your network. Packet sniffing is very useful when troubleshooting network connections. It can show you information like the size of packet data sent and received, headers, set cookies and cookie values, and even *yikes* if sent over HTTP (unencrypted), form data including site login details.
Packet sniffing helps you do a lot of detective work specifically around what is sent over the network. This means it can help you troubleshoot everything from bandwidth usage spikes to identifying network security issues.
That being said, packet sniffers can also be used by hackers and users with malicious intentions to “listen in” on your network. This is one reason why HTTPS is so important–it encrypts the data being transmitted between the web browser and the web server for your site.
Using ngrep to packet sniff
Now let’s dive into some usage examples of ngrep. Please note, in order to use ngrep you will need to be using a compatible operating system (Linux and Mac OS X are both supported), and you will need root access on your server.
Start by connecting to your server via SSH and entering a sudo screen. If you’re not familiar, you can open a sudo screen with the following command, provided you have the right access level:
sudo screen -S SCREENNAME
Once you’re logged into your screen, start simple by watching any traffic crossing port 80 (HTTP traffic is processed by this port):
ngrep -d any port 80
You’ll notice some information flowing across the screen (providing the server is receiving some traffic on port 80 currently), but a lot of it will be super unhelpful junk like this:
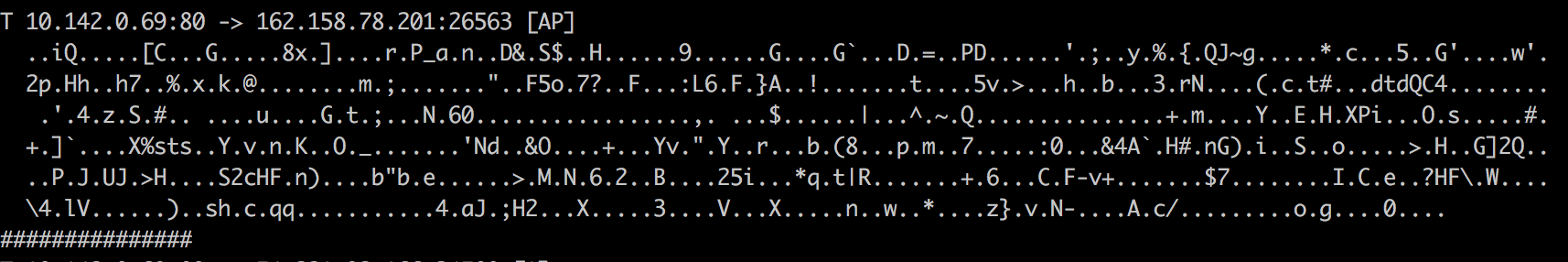
In order to get actually useful information we’ll need to filter the results. Let’s try separating it out with “-W byline” instead, and filter for only results that include “GET /” on port 80.
ngrep -q -W byline -i "GET /" port 80
This should yield some more readable results. You should now see lines for headers, remote IP addresses, and set cookies.
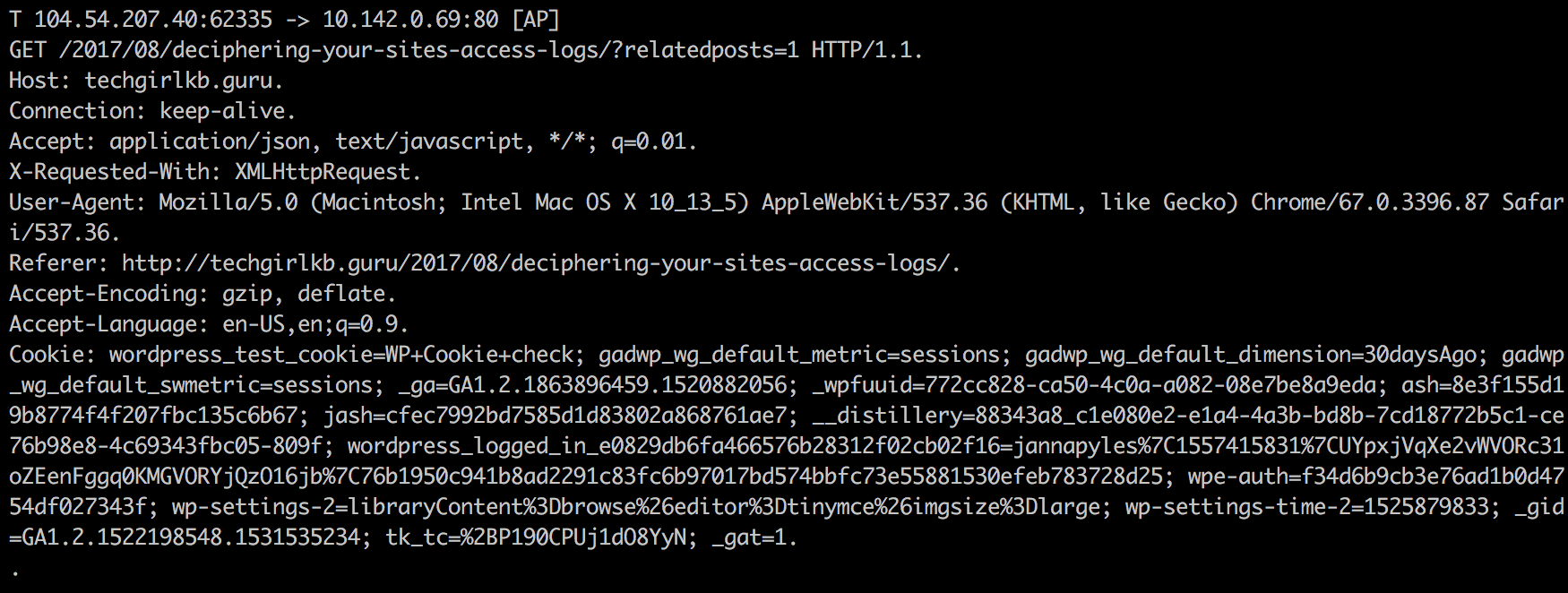
Using this same syntax you can grep for more things, like for example:
ngrep -q -W byline -i "POST /wp-login.php" port 80
Be aware, the command above will show any username and passwords sent from the browser to the web server in plain text. However, if you are using SSL/TLS encryption to serve your website via HTTPS instead, this information will be sent over port 443 instead and will be encrypted. A great example of why SSL is so important!
ngrep options
Once you learn the basics like the examples above, you can experiment with the optional flags available with ngrep. Below are some examples of interesting and helpful flags available, though you can find the full list on the MAN page.
-e – show empty packets as well. Normally these are discarded.
-W normal|byline|single|none – specify how you’d like to see the packet data. “Byline” is perhaps most useful in that it allows you to view the data mostly without wrapped content, making the packet entries more easily readable,
-O – dump the output to a file
-q – quiet mode. Only outputs the headers and related payloads.
-i – ignore case (matches UPPERCASE, lowercase, or MiXeD).
-n num – match only num number of packets before exiting.
-v – invert and instead show only things that DON’T match your regex.
host host - specify the hostname or IP address to filter for.
-I pcap_dump – use a file named “pcap_dump” as input for ngrep.
In conclusion
Ngrep can help is a helpful tool for monitoring and filtering packets of data sent over the network. I hope this guide has helped you learn more about ngrep! Have any favorite ngrep commands you use, use cases to share, or questions? Let me know in the comments, or contact me!
Leave a Reply